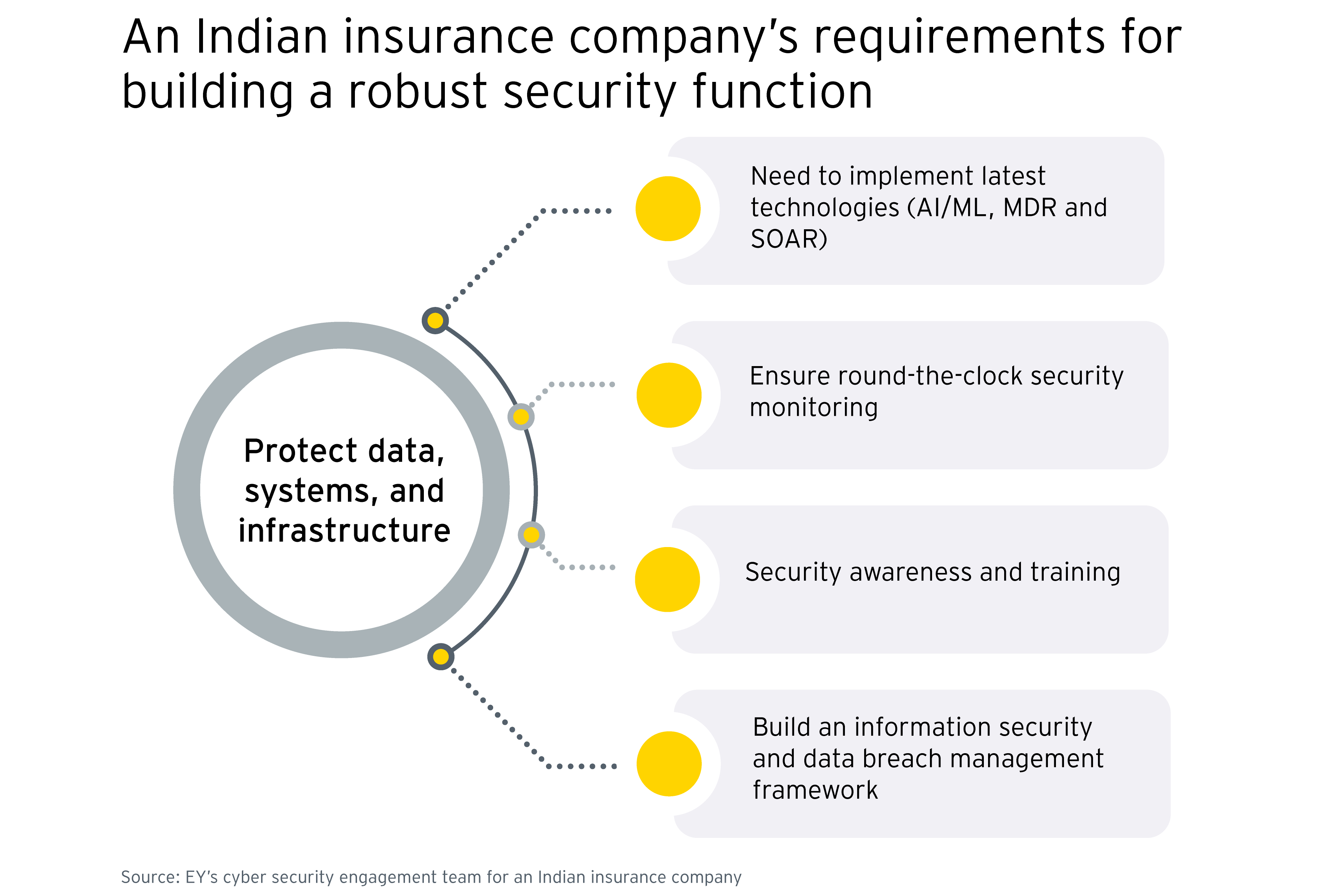
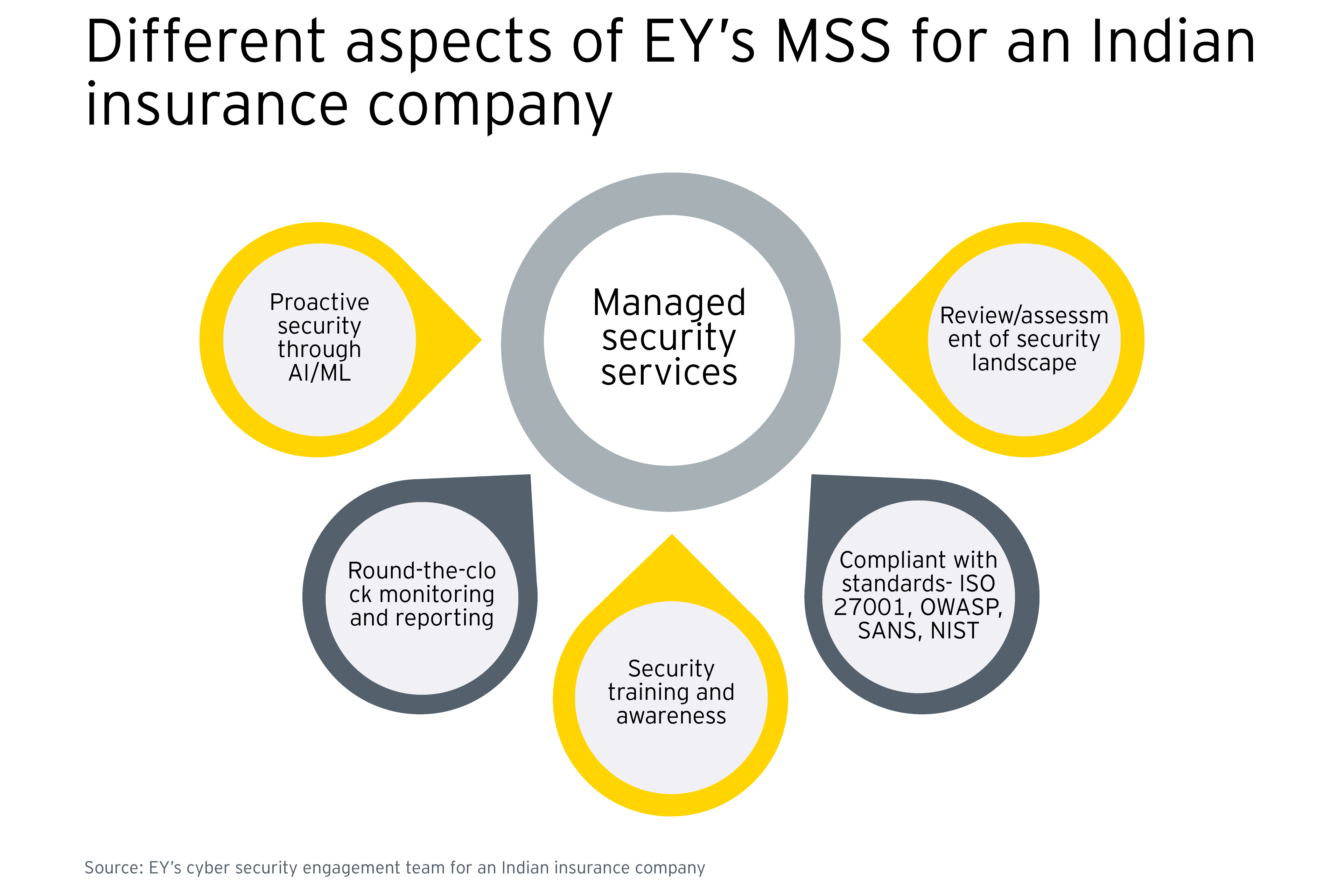
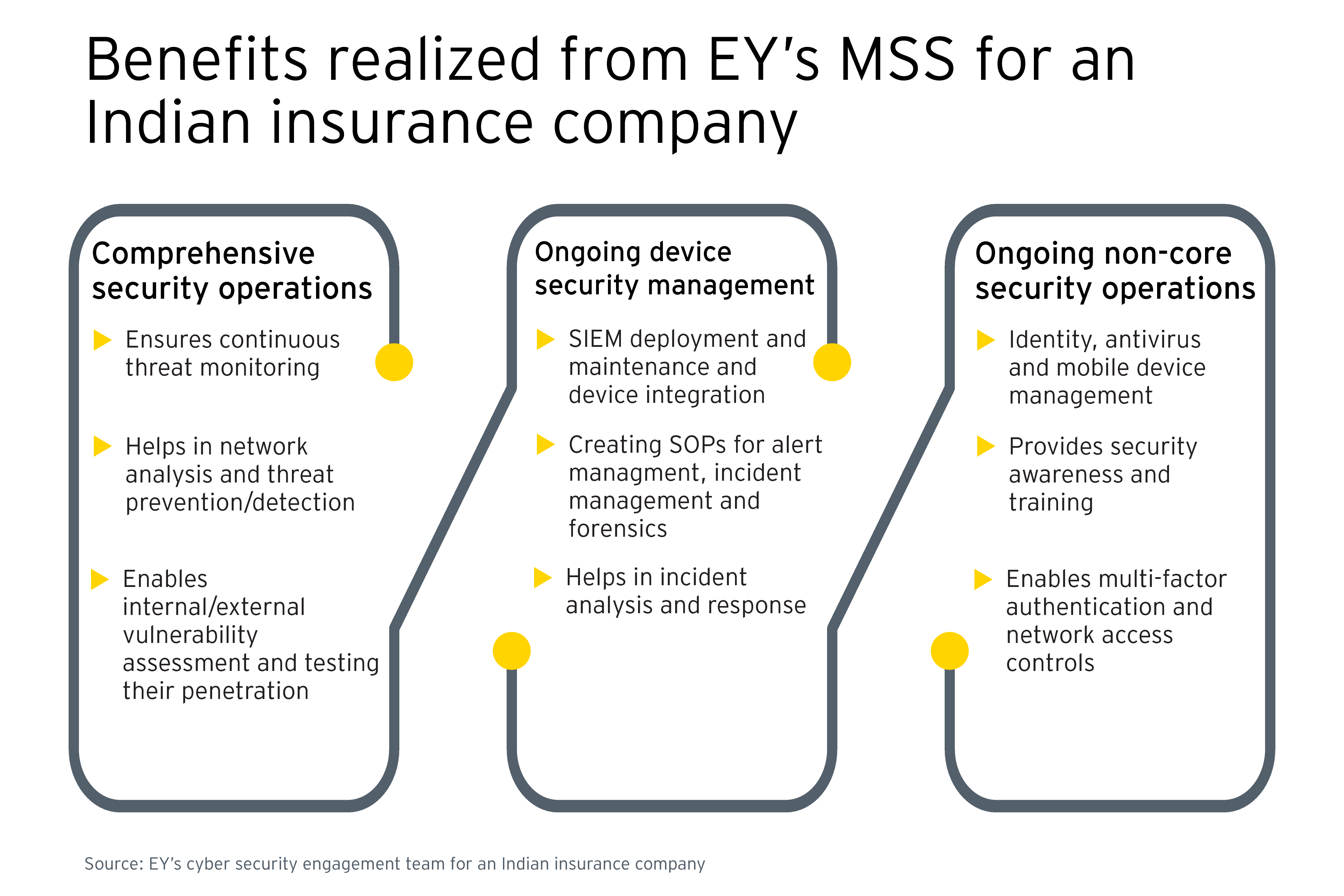
For AI/ML enablement, the company was looking for a reliable partner to deploy and operate the required capabilities. The company evaluated several parameters of a service partner, such as its vulnerability management capabilities, knowledge about the organization’s attack surface, and the presence of an established incident management process. As a reliable partner, EY established an MSS model at the company providing round-the-clock security monitoring and incident reporting.
As part of the deployment, EY implemented a security incident and event management (SIEM) process along with maintenance and integration. The solution was equipped with AI/ML capabilities which enabled the company to proactively monitor threats and determine response plans for cyber security breaches. The MSS model offers services through its Cognitive Capability Center (CCC), security governance services, and vulnerability management services.
EY also developed a security awareness program for the company offering training and awareness on cybersecurity. The MSS implementation is compliant with various industry and quality standards, including ISO 27001, OWASP, SANS and NIST.