EY refers to the global organization, and may refer to one or more, of the member firms of Ernst & Young Global Limited, each of which is a separate legal entity. Ernst & Young Global Limited, a UK company limited by guarantee, does not provide services to clients.
How EY can help
-
Data protection & privacy services at EY ensures data security, lifecycle management, compliance frameworks, risk assessment & strategic privacy solutions.
Read more -
Discover how EY's identify and access management (IAM) team can help your organization manage digital identities for people, systems, services and users.
Read more
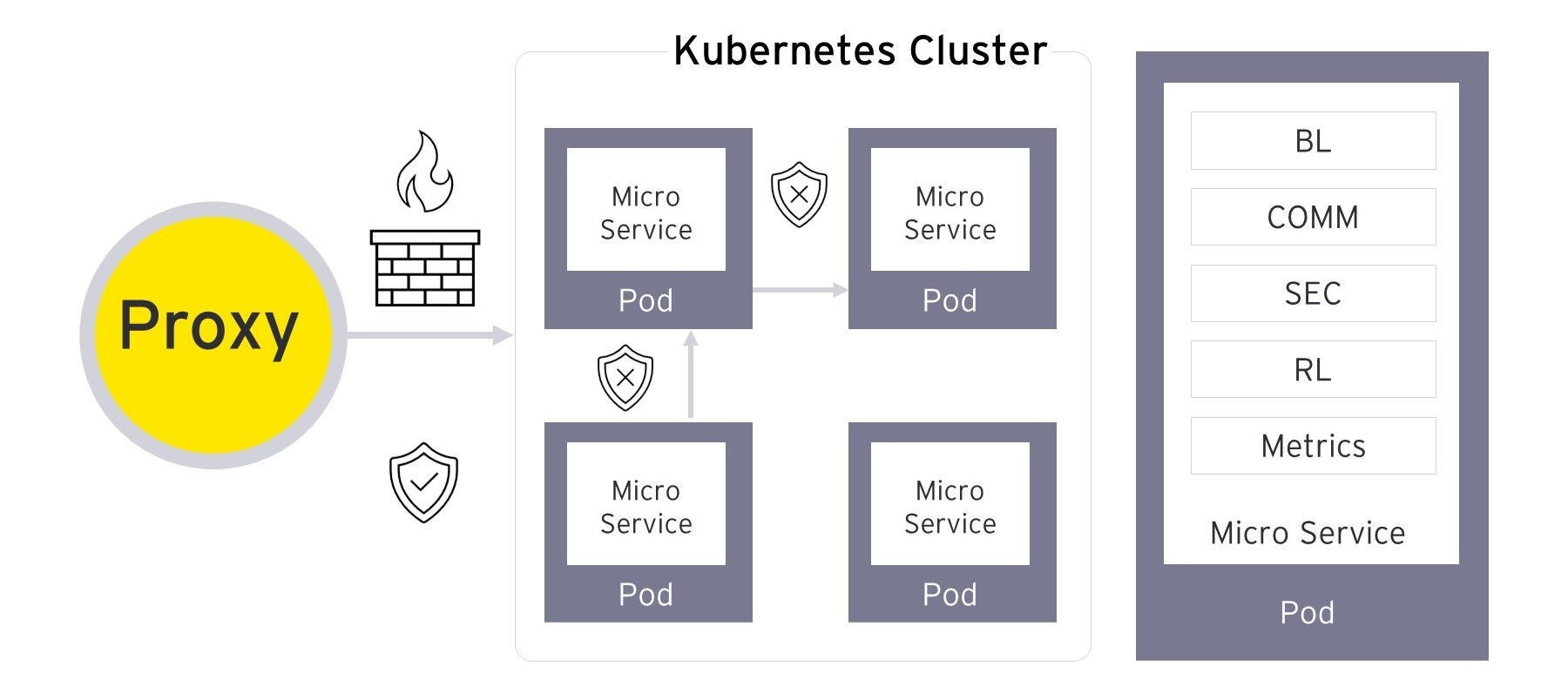
Microservices or microservices architecture is a cloud-native architectural approach in which a single application is composed of many loosely coupled and independently deployable smaller components or services. They communicate with one other using a combination of REST APIs, event streaming, and message brokers. Applications are evolving into collections of functions and microservices, with everything becoming described in code. However, it is a challenge to operationalize security rules that can function seamlessly across the various technologies that developers use to build and deploy cloud-native applications. To address these challenges, organizations must adopt an enterprise service mesh.
Service mesh ensures visibility
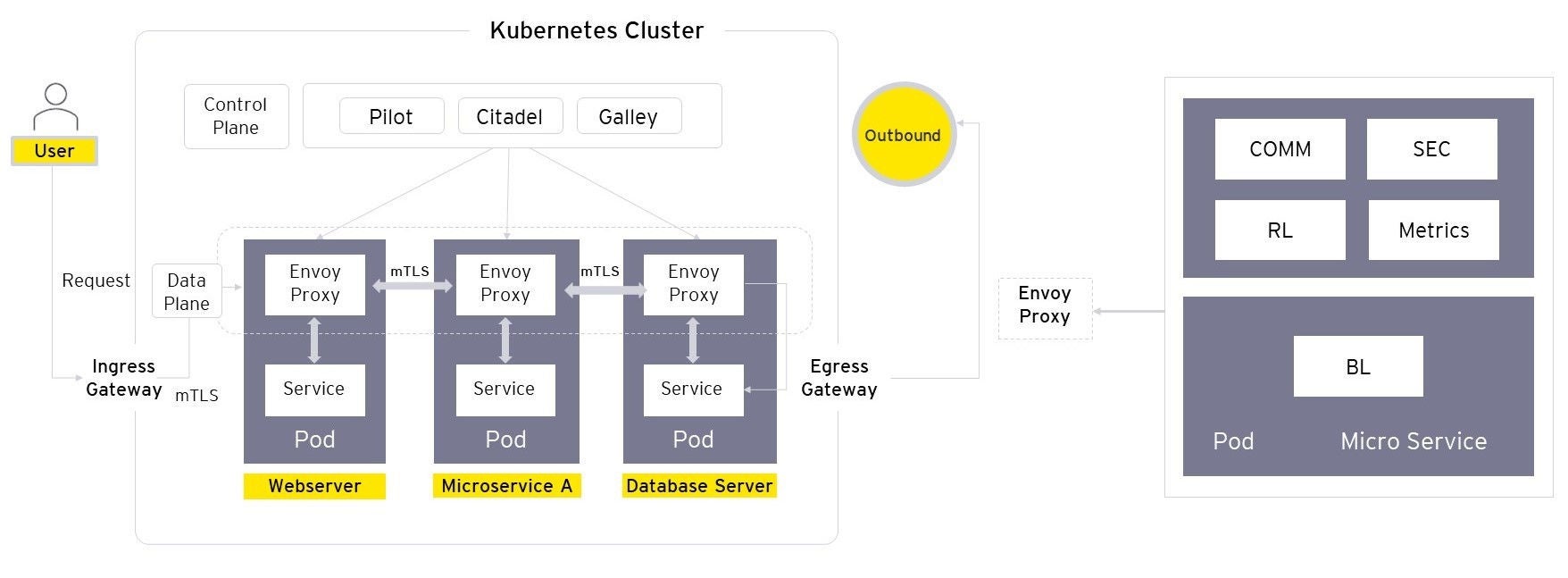
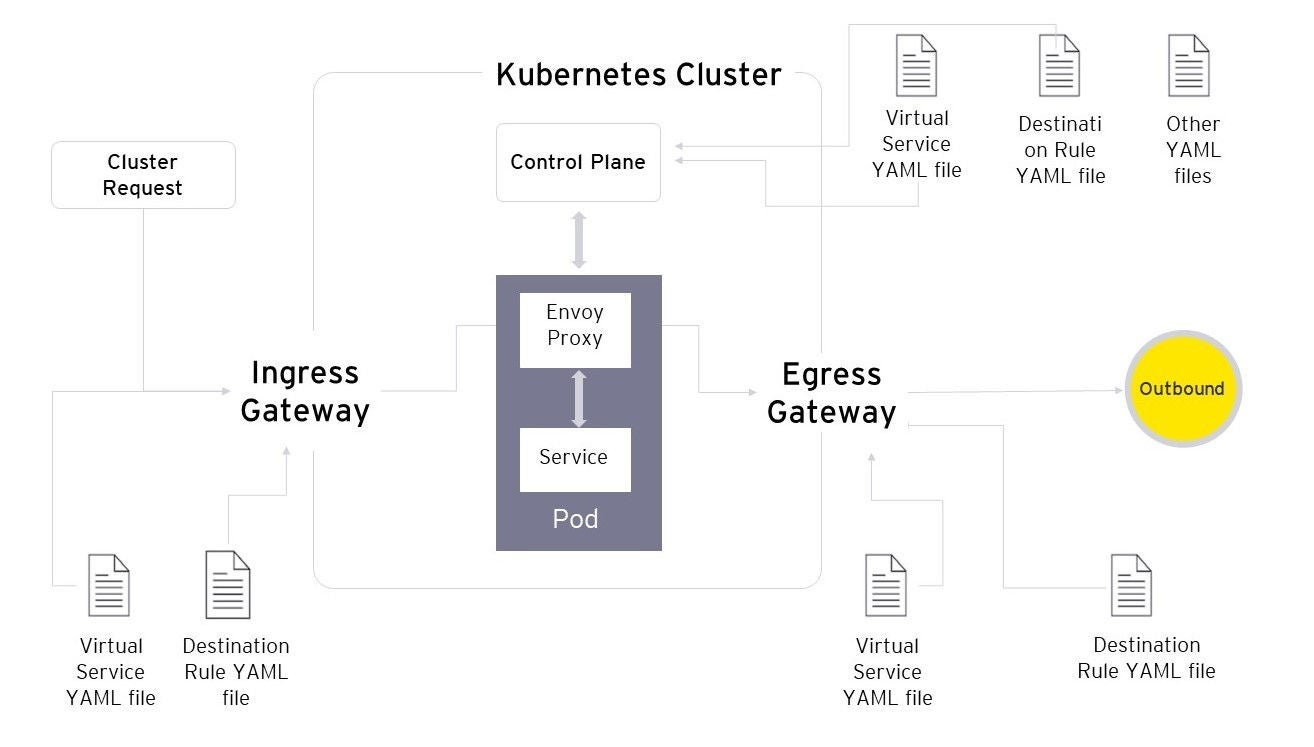
Implementing a service mesh provides certain functionalities to manage and control communication relationships between microservices. Whether it is out-of-the-box security features such as authentication systems for legitimate users, role- or attribute-based access control for authorized user actions, secure channel communications between services using Mutual Transport Layer Security (mTLS), or real-time policy enforcement for workload protection based on requirements and platform, enterprise service mesh platforms offer holistic security capabilities that can be implemented for all microservices at scale.
Service mesh platforms for enterprises come with deep visibility into application and microservice behavior, such as measuring, correlating, and mitigating Service Level Objective (SLO) violations, gathering consistent metrics for all apps, providing a single point of view for all microservices and their data flow in real time, among other salient features.