EY refers to the global organization, and may refer to one or more, of the member firms of Ernst & Young Global Limited, each of which is a separate legal entity. Ernst & Young Global Limited, a UK company limited by guarantee, does not provide services to clients.

Does your company have over 50 employees or an annual turnover of €10 million?
If so, you may be one of the thousands of companies affected by NIS2.
In brief
- The NIS2 will impact many EU companies operating withing critical sectors. If your organization is in scope for NIS2, here are the key things you should know:
- There are 10 cybersecurity risk management measures you must perform, and top management is responsible and accountable for your cybersecurity.
- A harsher penalty regime will be in place, a stricter supervisory regime will be adopted, and stronger reporting requirements will be set.
The NIS2 (Network and Information Security) Directive is the EU’s cybersecurity latest policy that aims to improve the collective cybersecurity of Member States. It repeals and replaces its predecessor, the NIS Directive, by including stricter requirements for security, stronger reporting obligations, and more severe enforcement requirements for a wider scope of organisations. In essence, NIS2 aims to protect critical organisations and infrastructure within the EU from cyber threats with the goal of achieving a high level of common security across the EU. To fulfil its objective, the NIS2 Directive focuses on organizations that operate in critical sectors, as they are essential for the proper functioning of society and, for this very reason, are often the primary target of cyber-attacks.
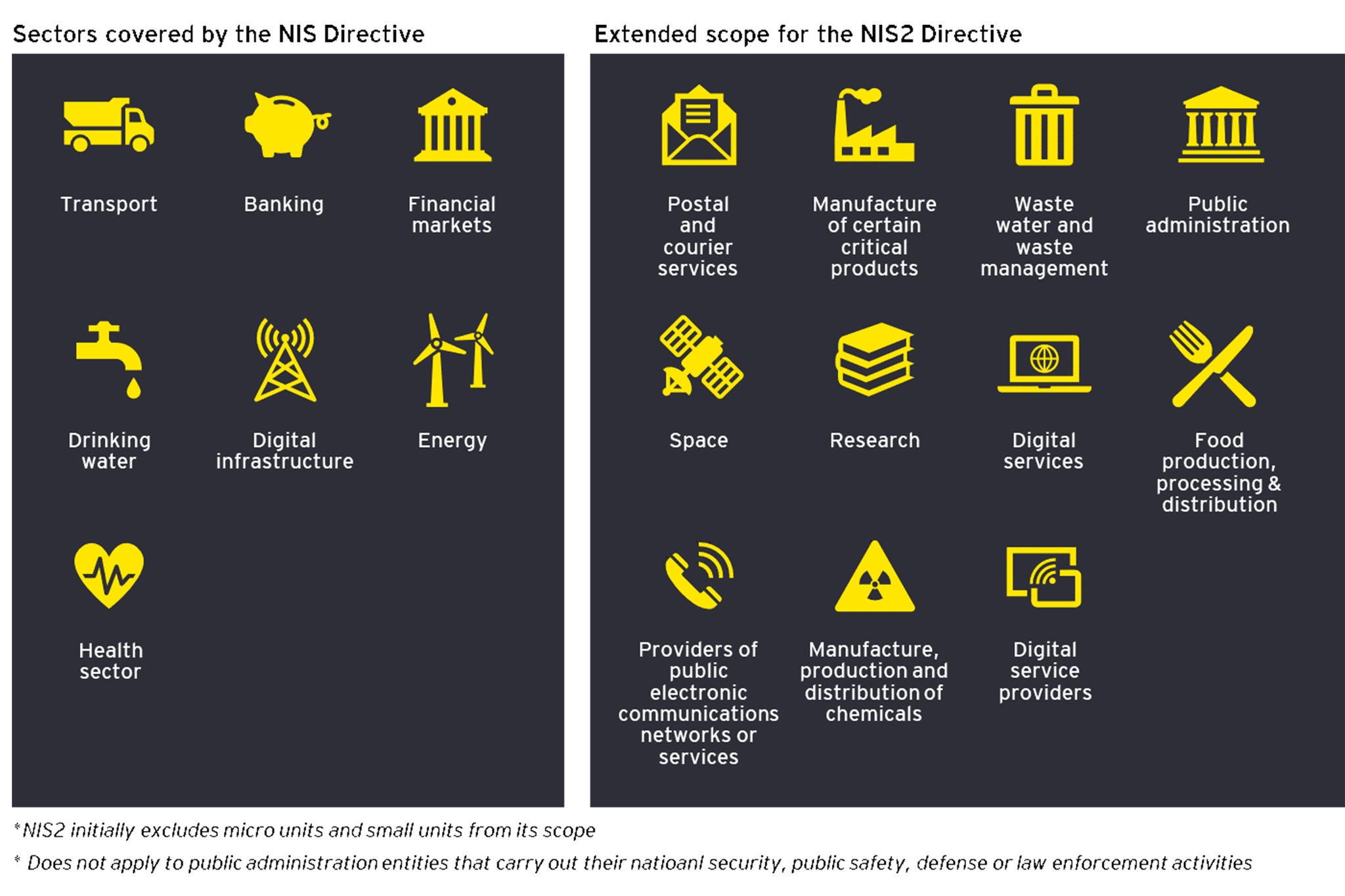
It is estimated that the NIS2 Directive will impact over 100.000 organizations across the EU in addition to those already within the scope of the first NIS Directive, as it increases its scope from seven sectors to eighteen:
If your organization is included in the scope of NIS2, there are five things you need to know and actions you must take to comply with the new requirements.
- There are 10 cybersecurity risk management measures you must perform. You are required to take appropriate and proportionate technical, operational, and organizational measures to manage the risks posed to the security of your network and information systems to prevent or minimize the impact of incidents on the recipients of your services. These measures include:
- Risk analysis and information system security policies
- Basic cyber hygiene practices and cybersecurity training
- Business continuity (such as backup management and disaster recovery) and crisis management
- Use of multi-factor authentication or continuous authentication solutions
- Policies and procedures regarding the use of cryptography and encryptionPolicies and procedures to assess the effectiveness of cybersecurity risk management measures
- Incident handling (prevention, detection, and response)
- Human resources security, access control policies and asset management
- Security in network and information systems acquisition, development, and maintenance
- Supply chain security measures
- Top management is responsible and accountable for your cybersecurity. The management body of your organization must approve the cybersecurity risk-management measures listed above, and will be required to follow cybersecurity training. Failure to comply with its cybersecurity risk management responsibilities may entail a temporary ban from exercising managerial functions.
- A harsher penalty regime. Failure to comply with NIS2 requirements will cause significant penalties. These may consist of fines of up to EUR 10 000 000 or up to 2% of total annual turnover and the suspension of authorization concerning the services you provide.
- A stricter supervisory regime. NIS2 has strengthened the supervisory regime to ensure compliance with all the security risk management requirements included in the directive. This means that your organization may be subject to on-site inspections and off-site supervision including random checks, regular and targeted audits, security scans, or request to access data, among others. The degree to which you will be supervised by authorities will vary depending on whether your organization is classified as an important or essential entity, with stronger supervision on the latter.
- Stronger reporting requirements. In case of a cyber incident, you will have to notify the incident to the relevant authority within 24h and create a report within 72h. This report must include a detailed description of the incident, the type of threat or root cause that likely triggered the incident, and the mitigation measures that you have applied to reduce the damage.
It is crucial that your organization is familiar with the cybersecurity requirements you must comply with, as failure to do so will lead to severe sanctions. However, it is also worth considering that the cybersecurity measures included in the directive are designed to help you protect your data, systems and processes. Therefore, compliance will not merely prevent sanctions, but also guide you towards achieving a cybersecurity maturity that will shield your organization from cyber-attacks with the potential of having devastating effects on your company and all the recipients of your services.
At EY, we suggest that organizations begin by understanding whether they fall under the scope of the NIS2 Directive, and if so, in what capacity. If you do belong to one of the industries included in the legislation, then there are several steps you can take to prepare for the upcoming requirements you will have to fulfil. For instance, (1) perform an inventory or audit of your entire architecture and systems landscape, in order to successfully establish an adequate start off point for your risk management processes, (2) implement a risk management framework ensuring that threats against your data are continuously identified, assessed, evaluated, and treated, (3) initiate crisis management activities to limit the impact and duration of a crisis, (4) define and establish business continuity and disaster recovery procedures to ensure that your critical processes continue to operate at an acceptable level during a disruption, (5) make sure top management is involved in the cybersecurity strategy of your organization, (6) identify supply chain risks by including suppliers and service providers in your risk assessments, or (7) define a structured incident management process to successfully document, investigate, and classify cybersecurity incidents if/when they occur. All these activities will, not only guide you towards NIS2 compliance, but also strengthen your cybersecurity posture and build your resilience against the ever-increasing cybersecurity threat landscape.
Summary
The NIS2 Directive is a new EU cybersecurity policy that replaces the previous NIS Directive and aims to improve the collective cybersecurity of member states. It has a wider scope, covering 18 sectors, and requires organizations to mature their cybersecurity competencies. However, at EY, we promote the idea that compliance with the NIS2 Directive will not only prevent sanctions but also strengthen an organization's cybersecurity posture and build resilience against cybersecurity threats. Therefore, we suggest that organizations under the scope of the NIS2 Directive should already now begin to take the first steps towards the fulfilment of NIS2 requirements.

