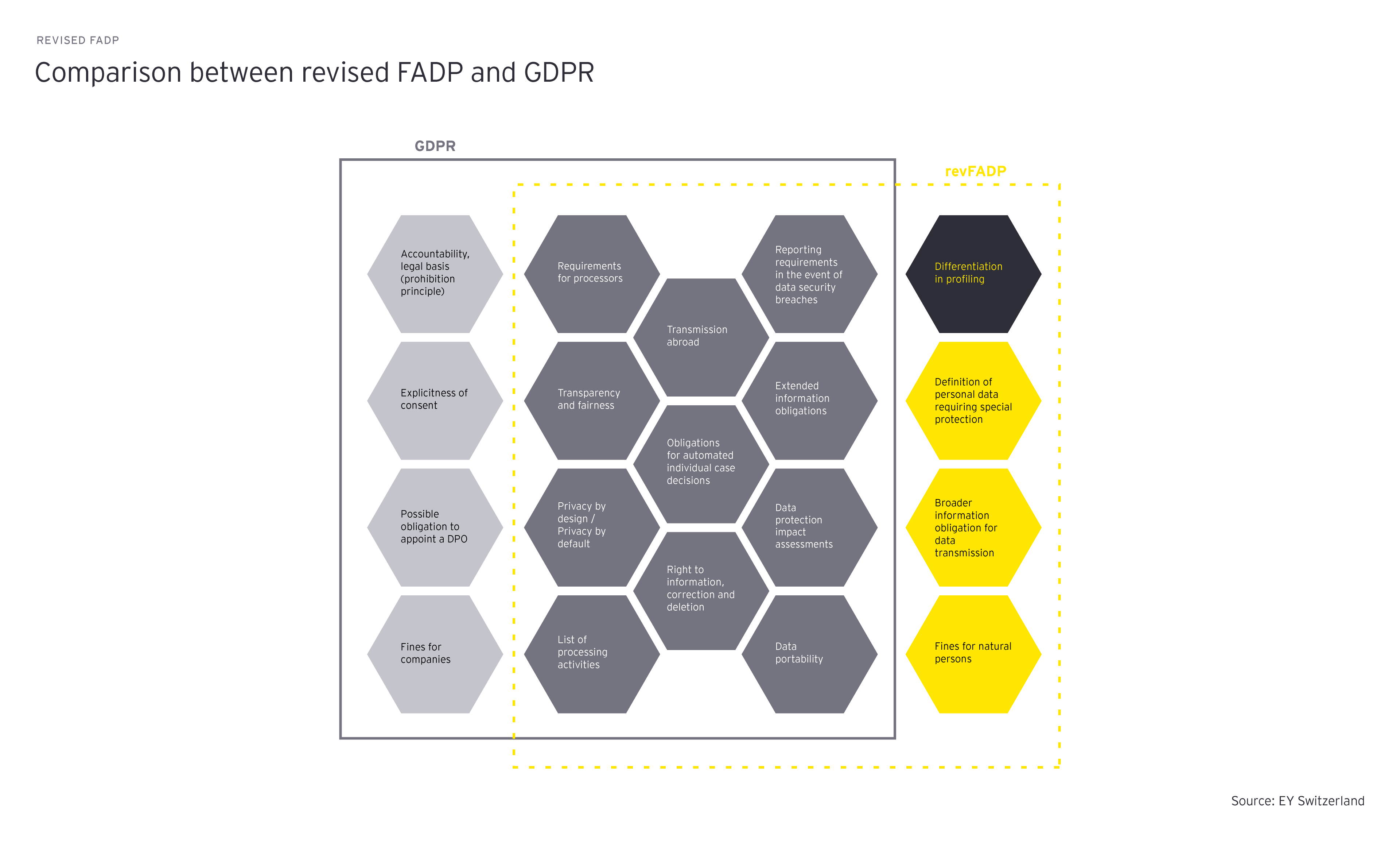
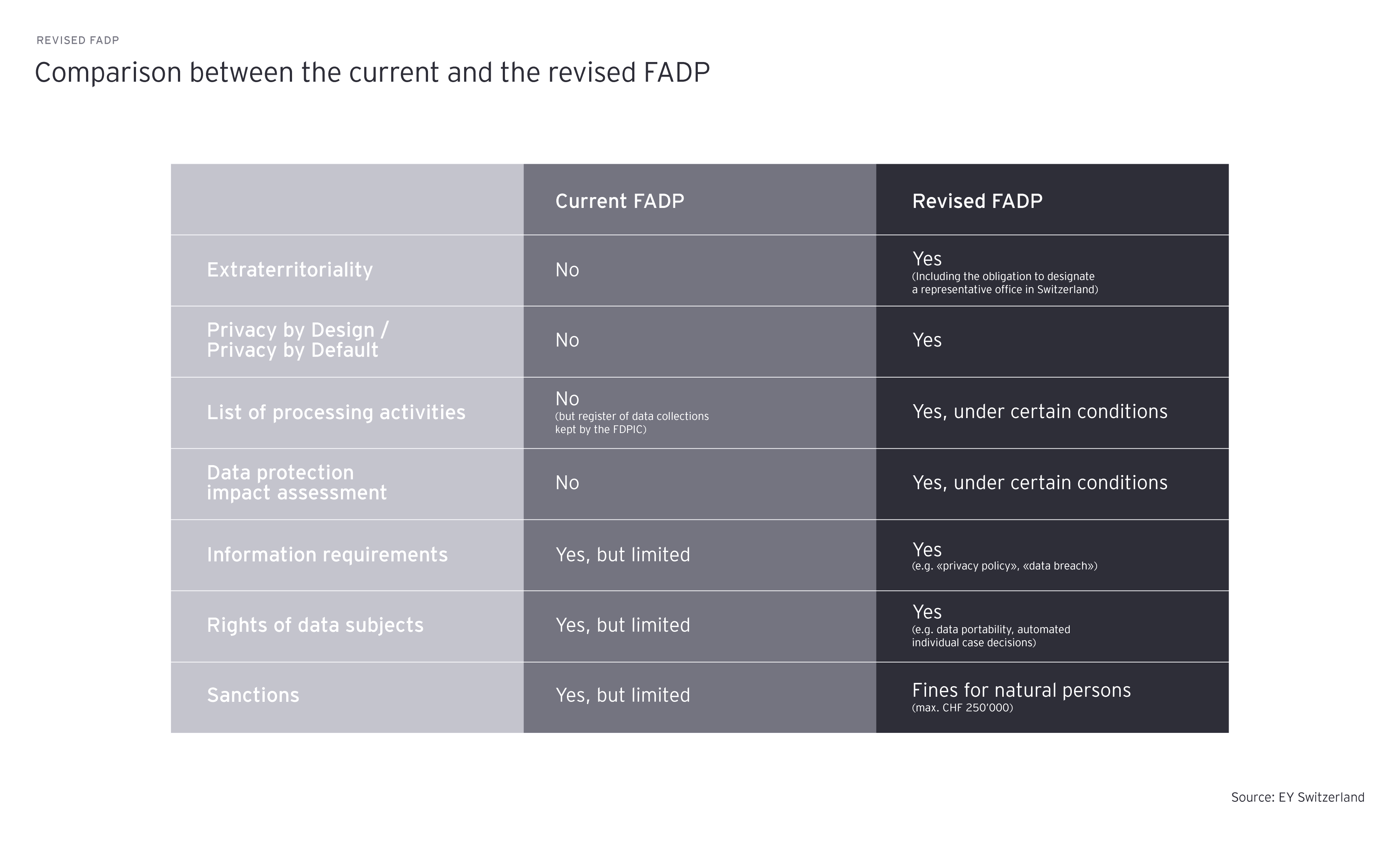
In the revised FADP, the information obligations are expanded. In the old FADP, there was already an obligation to provide information. However, this only applied to the procurement of particularly sensitive personal data or personality profiles. With the new data protection act, the person responsible for the data must inform each time personal data is obtained, provided none of the exceptions according to Art. 20 of the revised FADP exist. According to the revised FADP, the data subject must be provided with the following minimum information when obtaining personal data:
- Identity and contact details of the person responsible
- Purpose of the processing
- If applicable, recipients or categories of recipients to whom personal data may be disclosed and recipients to which personal data are disclosed
From an IT perspective it also makes sense to define a process for the transmission of personal data in a suitable electronic format. This process should cover the right of data subjects in case of a data breach, the right of data transmission, the right to be forgotten, the right to restrict data processing and more. Especially data processing applications have to support this process, which can be a challenge in case of unstructured data (e.g., when using files on file shares, analog files i.e., paper, audio, pictures, scans stored on SharePoints etc.).