EY refers to the global organization, and may refer to one or more, of the member firms of Ernst & Young Global Limited, each of which is a separate legal entity. Ernst & Young Global Limited, a UK company limited by guarantee, does not provide services to clients.

ICT organizations are leading digital advancements in the world, but this advancement is actually exposing many areas of risk.
In brief
- Defined framework assists ICT organizations across the world to enhance their security posture.
- Innovative developments and new business models provide additional entry points for cyber attacks.
- Organizations in the ICT sector are recommended to relook at their strategies and defense mechanisms to better counter cyber threats impacting their environment.
Empowering and enabling leading digital nations across the world requires an approach based on security by design where security is factored from the onset of all technology projects. Ground-breaking innovations within the technology world, quite often led by ICT organizations, are altering businesses and business models, connecting people with services that offer comfort and flexibility, and requiring entire industries to reimagine their futures.
The rapid digital advancements that the ICT organizations are making and the disruption it brings increase the risk of a cyber attack. Digitalization allows ICT organizations to deliver unique and connected data-driven and in-demand client experiences at a rapid pace, which leads to greater inherent cyber risks.
The challenges ICT organizations across the world are facing have been considered and bottlenecks, as well as inherent risks within business models, have been addressed through the issuance of a cybersecurity framework. The framework encompasses four key domains which are essential for cyber defense and resilience. The framework is supported by a number of guidelines that cover each identified domain in depth and provides a consistent methodology for attaining a target level of cybersecurity maturity that is commensurate with the organization’s risk levels.
It is a well-known fact that digital transformation is the catalyst for the proliferation of more services, experiences and benefits to customers — bringing increased revenue opportunities as well as risks. Cybersecurity is especially critical for ICT organizations across the globe due to the following inherent business issues and risks:
- Digital: The intrinsic nature of many ICT products and services makes cybersecurity particularly challenging for ICT organizations.
- New business models: The growing adoption of direct-to-consumer (D2C) models means ICT organizations will shoulder unprecedented end-to-end cybersecurity risks.
- A connected world: More devices are connecting to the internet and each other through the IoT, exponentially increasing the number of potential entry points for cybercriminals.
- Data-driven customer experiences: ICT organizations collecting more data provides a real competitive advantage for organizations and forces a balancing act to ensure customer trust and loyalty while protecting their customer base and their business.
- Lower customer switching costs: Many ICT segments have lower customer switching costs than traditional industries. Customers can quickly and inexpensively move to alternative providers if ICT organizations have real or perceived cybersecurity vulnerabilities.
Framework development
As part of the framework development, a series of activities are conducted, including but not limited to performing a current state assessment, gap analysis and benchmarking exercise. The conduct of such activities ensures that the final outcome considers the nuances of the sector, current challenges of the ICT organizations, missing control gaps and best practices observed in all regions across the globe.
The starting point of the framework development is to understand that a one-size-fits-all approach is not ideal for a complex and evolving ICT sector. The ICT sector is undergoing rapid changes and technological advancements as part of the dynamic vision of organizations across the world and due to the innovation landscape and trends that can be observed globally.
Therefore, ICT organizations should be encouraged to adopt a level of cybersecurity maturity that is commensurate with the complexity level of the organization being assessed. The structure of the framework, essentially the building block or foundation, should be brainstormed extensively, given its significance, and should ultimately result in a six-layered model (as shown below).
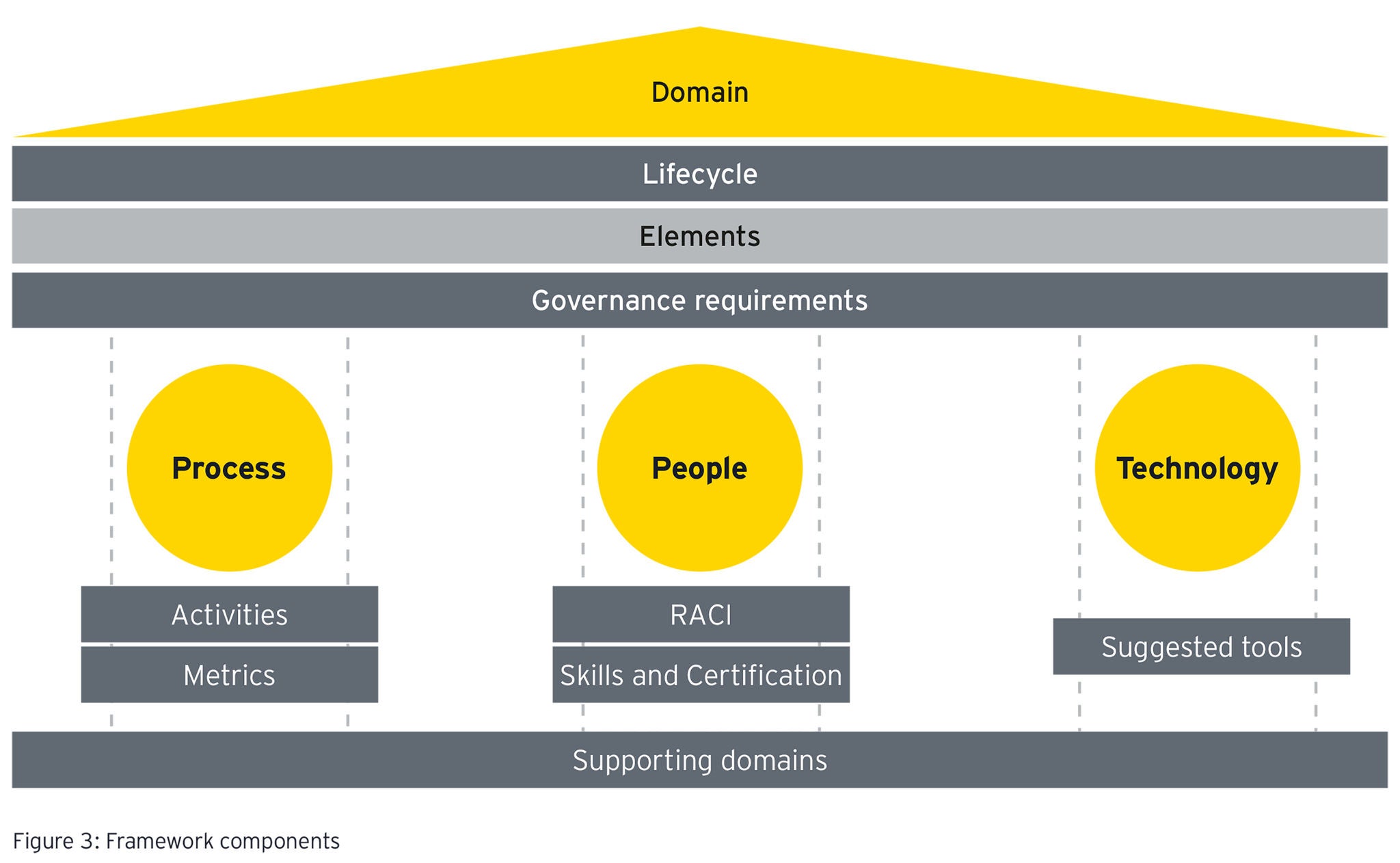
The framework should also comprise of four suggested domains that are essential for an effective cybersecurity defense program: vulnerability, threat, incident and crisis management.
ICT sector landscape
As more and more nations launch a new generation of giga-projects and accelerate their modernization effort to create a sustainable, investor-friendly business environment, an onslaught of digital technology is unavoidable. The push to establish the foundations of a digital nation is stronger than ever, and it will necessitate high levels of collaboration among ICT businesses, which are the essential facilitators of a digital nation-state. Shifting industry dynamics and evolving digital transformation plans across the world are continually prompting organizations internationally to innovate and explore new technologies and delivery models.
With many digital transformation initiatives in the ICT sector globally, the significance of cybersecurity for the nation’s economy and outcomes for citizens and enterprises is humongous. Multiple initiatives should be undertaken to enhance the overall digital cybersecurity posture of the nations and the ICT sector, such as the establishment of a national cybersecurity authority, an ICT sector-specific cybersecurity framework and a national cybersecurity strategy.
VTI and CM framework essentials
How to develop the framework and guidelines?
1. Develop LPL
Although the ICT organizations at the global level are rapidly growing, they might remain mostly underdeveloped in terms of cybersecurity procedures. As per interviews with key stakeholders of organizations, it was observed that many organizations and their employees have yet to completely comprehend their cybersecurity duties and obligations. While the need to perform a current state assessment should be evident based on internal discussions, the challenges might remain in terms of identifying the best possible way to go about it. By performing multiple brainstorming sessions, it can be agreed that a Leading Practice Library (LPL) should be defined and consist of good cybersecurity practices and also leveraging industry standards such as ISO (International Organization for Standardization) 27001, NIST CSF (National Institute of Standards and Technology Cybersecurity Framework) and BS (British Standards) 11200.
2. Current state analysis
Having designed the methodology and approach to conduct a current state analysis, the next step involves identifying a set of organizations that will form part of a pilot assessment. To ensure smooth conduct of the pilot exercise, it is recommended to use a digital tool to capture the responses of the organizational representatives and assist in consolidating responses across the pilot organizations. The responses are collated to prepare dashboards that provide a sector-wide view as well as a company-level view, to assist the nation and the organizations to understand the existing cybersecurity posture.
3. Benchmarking
Benchmarking is for respective countries to understand effective cybersecurity procedures developed by other nation-states (and possibly their critical sectors) and global practices. While the necessity is obvious, the procedure for conducting the benchmarking exercise needs to be addressed and finalized.
4. Gap analysis
The gap analysis is based on outcomes obtained through company profiling, domain assessment performed for a sample set of IT companies and results obtained by comparing the nation’s current capabilities to leading global cybersecurity practices observed within the benchmarked countries.
A gap analysis report should be generated based on the analysis and should highlight the key areas of improvement observed with regards to the four cybersecurity domains. The gap analysis should be divided into two sections: gap analysis at the national or sectoral level and gap analysis at organizational level.
5. Framework and guidelines
In order to enhance the digital cybersecurity posture of the ICT sector, the nations should embark on a path that ultimately contributes to the development of a framework and guidelines that comprises four domains: vulnerability, threat, incident and crisis management. The issuance of the framework and the associated guidelines is for the companies to achieve the required level of maturity and to build a robust infrastructure along with the necessary cybersecurity controls.
Conclusion
Sectoral cybersecurity frameworks are a trend which will continue to grow given that they take into consideration sector-specific technical know-how and expand from a national framework that is more tailor-made to meet the needs of the sector. We believe the EY approach in defining the framework along with a set of guidelines that support the implementation of the framework is leading, as it not only considers the size and complexity of the company but also addresses the needs and requirements of industry standards, applicable regulatory frameworks. It is important to note that a one-size-fits-all approach will not necessarily work in a dynamic and volatile sector such as the ICT. Therefore, a tailored approach that considers the size and complexity of the organization in question is assessed prior to identifying the required level of maturity. So, it is important for sectoral authorities to understand the crux of this framework and pay heed to the level of details and granularities the ICT sector framework and guidelines dive into. To be cyber resilient, organizations need to constantly quiz relevant stakeholders with regards to the cyber attacks which might affect the various units and consider cybersecurity risks and threats throughout the lifecycle of technology implementation.
Related articles
Building trust through digital transformation
MENA organizations can leverage the evolving cyber threat to establish themselves as trusted brands through excellence in cybersecurity.
How GCC companies can use data to close trust gaps
As companies understand and explore the need to collect data, here are five ways to harness the business imperative of building trust.
Summary
ICT organizations are the catalyst for enabling digital transformation and large-scale changes across all industries and sectors around the globe. The article deep dives into the approach undertaken for developing the framework and provides insights into the leading practices that could be considered by similar entities developing sectoral cybersecurity frameworks globally. The focus is on enhancing the cybersecurity posture of the ICT sector at a rate that is commensurate with the rapid advancements in technology and innovation across the global ICT sector. To guide ICT organizations regarding methods to upscale cybersecurity maturity, a series of activities have culminated on how ICT organizations and sectors can prepare a framework and guidelines that cover the essential topics of vulnerability management, threat management, incident management and crisis management.





