
What does the updated ISO 27002:2022 mean for you?
ISO27002:2022 introduces drastic changes to the ISMS framework structure. These will have an impact on future ISO 27001 certifications or recertifications. There are certain steps you can take to overcome the new challenges created by the updated ISO 27002 standard.
A new version of the ISO 27002 standard was released on February 15th, 2022, replacing the text released in 2013. Despite several structural modifications, the purpose of the document remains the same and provides a set of generic reference security controls to use within the context of an Information Security Management System (ISMS) based on ISO/IEC 27001.
The ISO/IEC 27001 has not been updated yet, although we expect the ISO/IEC DIS 27001 to replace the 2013 version on the official ISO website. The new text is still under development in the official ISO “Enquiry” phase.
This article looks at the details of the ISO 27002 changes and the impact on the security organization, as well as your ISMS and ISO27001 certification.
Key changes: A new structure and updated security controls
From fourteen to four domains
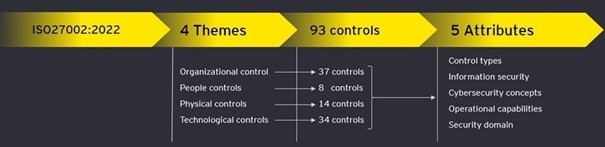
The most noticeable change is the new structure of the document. Previously, the suggested controls were grouped into fourteen domains, as opposed to 4 themes now:
- Organizational controls (clause 5)
- People controls (clause 6)
- Physical controls (clause 7)
- Technological controls (clause 8)
Furthermore, there are 2 annexes:
- Annex A – Using attributes
- Annex B – Correspondence with ISO/IEC 27002:2013
Fewer security controls due to consolidation
Another noteworthy change is the reduction of the number of security controls from 114 to 93. This is primarily the result of their consolidation. Out of those 93, there 58 updated controls, 24 merged ones and 11 new ones.
Overview of the eleven new controls
The following security topics were previously described across multiple controls. In the latest version, these topics received their own control with detailed purpose and guidance:
- 5.7 Threat intelligence
- 5.23 Information security for use of cloud services
- 5.30 ICT readiness for business continuity
- 7.4 Physical security monitoring
- 8.9 Configuration management
- 8.10 Information deletion
- 8.11 Data masking
- 8.12 Data leakage prevention
- 8.16 Monitoring activities
- 8.23 Web filtering
- 8.28 Secure coding
The three most impactful controls are the following:
- Secure Coding: A constantly increasing number of companies develop software. Poorly written code can result in critical vulnerabilities (e.g. absence of input validation can lead to XSS attacks, SQL injections, etc.). Technical control “8.28 Secure coding” provides secure coding principles that you should apply to software development.
- Threat Intelligence: One of the key aspects of securing your organization is identifying possible threats. You can calculate the risk related to each identified threat and implement mitigating measures. Organizational control “5.7 Threat intelligence” refers to collecting and analyzing information related to information security threats. It considers strategic, tactical and operational threat intelligence.
- Information security for use of cloud services: Companies are moving to cloud environments at a rapid pace. Organizations often assume that most information security risk lies with the cloud service provider. However, this is usually not the case. Organizational control “5.23 Information security for use of cloud services” provides guidance for acquiring, using, managing and exiting from third-party cloud services. It states that you must clearly define the responsibilities of the cloud service provider and the organization.
Introduction of attribute values for each control
The last major change is the introduction of five attributes along with their respective values.
- Control types: #Preventive, #Detective and #Corrective
- Information Security Properties: #Confidentiality, #Integrity and #Availability
- Cybersecurity concepts: #Identify, #Protect, #Detect, etc.
- Operational capabilities: #Governance, #Asset_management, #Information_protection, etc.
- Security domains: #Governance_and_Ecosystem, #Protection, #Defense, etc.
Annex A – “Using attributes” links one or more values from every attribute to the 93 security controls, which allows for easy grouping and sorting. For example, when an organization wants to strengthen their preventative controls, they can filter on the “#Preventive” value within the “Control types” attribute to obtain a list of reference preventative controls.
Annex B – “Correspondence with ISO/IEC 27002:2013” is retroactive with the 2013 version, allowing for a smooth transition to the 2022 version.
Impact on your security organization
The new security controls defined in ISO 27002 may already exist in other standards and frameworks. However, it is important to acknowledge these updates as many organizations are using ISO 27001 and 27002 as the cornerstone of their information security management system. By aligning your security controls to the new ISO 27002, you align with industry best practice. Your security infrastructure may thus benefit from these new introductions, and you should consider integrating these controls (if not yet done as part of alignment with existing regulations, standards or frameworks).
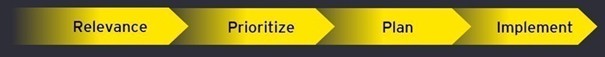
You can take the following steps to comply with the new ISO 27002:
Relevance: A gap analysis is one way to map out and understand the differences between the current controls in place and the best practices according to ISO 27002.
Prioritize: By prioritizing the most relevant controls, companies will be able to focus their efforts and enhancing their security posture.
Plan: Create a timeline that shows when controls will be implemented and calculate how much the implementation of the tools will cost.
Implement: The final step is the actual implementation of controls and integration of the organizations’ security capabilities & ISMS.
Certification
As with previous versions, it is still not possible to obtain a certification for the new ISO 27002. However, it has important guidelines and best practices to help organizations better comply with the ISO 27001 and obtain the ISO 27001 certification.
If your organization already has the ISO 27001 certified and you want to keep it, you should perform the following steps.
- First the scope of your ISMS and risk assessment should be re-evaluated.
- Secondly, you should check whether any of the updated and new controls are relevant in mitigating any risk you would like to lower.
- Finally, you should implement these controls. The ISO 27001:2013 will still be valid during a transition period, although it has not yet been released how long this transition period will be. Looking at previous transition periods, we can expect a 24-month duration.
For companies looking to be certified under the next ISO 27001, they can get a head start by already understanding and updating their ISMS along with defining and prioritizing the significant changes that would impact the current controls in place.
Internal resources such as your internal audit department may already consider reviewing the implementation of the newly introduced controls before the official updated certification date. In case no specific expertise is available, external resources may help on this matter as well.
Nevertheless, it remains important to test these controls in accordance with industry best practices and to understand any major changes to (implemented) controls. The newly introduced attributes for these controls will support Internal Auditors or external assessors to plan out the audit in a more structured way by considering the control domains, type, and properties.

