EY refers to the global organization, and may refer to one or more, of the member firms of Ernst & Young Global Limited, each of which is a separate legal entity. Ernst & Young Global Limited, a UK company limited by guarantee, does not provide services to clients.
How EY can help
-
Discover how EY-Parthenon tech-enabled Advanced Analytics teams help turn information into connected intelligent insights.
Read more
Shifting winds in the financial sector
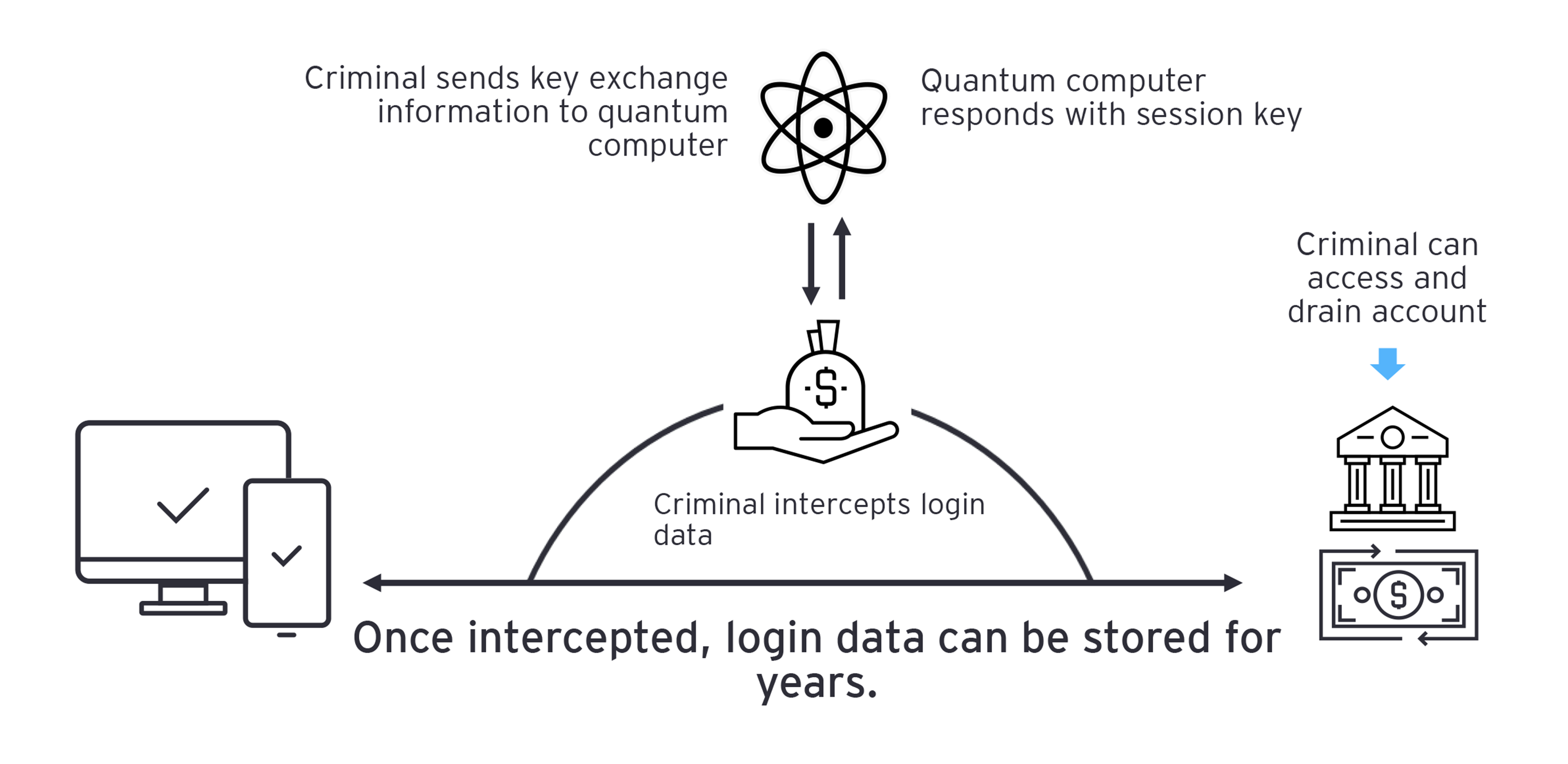
Forecasts for the arrival of cryptographically relevant quantum hardware are getting shorter, and the financial services industry is starting to shift its attitude. Rapid advancements in quantum capabilities, an increasing amount of attention from government agencies and regulators, and several high-profile cyber attacks on financial institutions have highlighted the urgency for deploying more robust security measures. Major credit and debit card payment organizations have recently applied quantum-resistant technology to the next generation of payment protocols. The new enhanced-contactless (Ecos) specifications go beyond industry standards to ensure that transactions are resistant to attacks from both traditional and quantum threats. Mastercard has already introduced cards with these new specifications,⁵ giving consumers high levels of “future-proof” security for decades to come. Beginning to realize the immense security threats, the world’s largest global banks are also placing big bets on talent, intellectual property and strategic partnerships surrounding quantum security. For example, JP Morgan Chase demonstrated a first-of-its-kind, production-grade quantum key distribution (QKD) network,⁶ a mathematically proven way to defend against quantum attacks. The fact that a financial services organization led a technological effort of this magnitude underscores how paramount quantum security will be.
This preparation is sound business; the consequences of inaction are difficult to overstate. The 2014 breach of a major financial institution⁷ by foreign hackers exposed a web application vulnerability that allowed access to sensitive information belonging to 76 million households and 7 million small businesses. The affected bank spent $250 million annually on cybersecurity to remediate the breach, in addition to settling a class-action lawsuit for $80 million. Similarly, in 2019, a misconfigured firewall at a different bank resulted in the release of social security and bank account numbers of over 100 million customers. This incident cost the bank more than $200 million in remediation, including class-action lawsuit settlements and credit monitoring for affected customers.
These breaches not only resulted in significant financial harm but also damaged the organizations' reputation and customer trust. They further prompted the passage of increased regulatory oversight, including the Cybersecurity Information Sharing Act and the New York State Department of Financial Services Cybersecurity Regulation, requiring financial institutions to have a robust cybersecurity program in place, including periodic risk assessments, vulnerability testing and incident response planning. Despite these regulations and updated security methods, financial organizations are still vulnerable to new, quantum-based attack vectors, drastically increasing cyber-risk and demanding immediate attention.